Regular browsers can’t open Onion sites because they aren’t part of the standard domain name system. They facilitate secure communication over the web and protect from third-party surveillance. The above configurations help improve your security when surfing the web via Tor.
- Once Tor Browser is successfully connected to the Tor network, users can begin to explore what are known as onion services, often referred to as websites on the dark web.
- These updates often address known vulnerabilities that could be exploited by malicious actors on the dark web.
- You can use search engines like DuckDuckGo or Torch to find the websites you want.
- It uses the onion router to bounce your signal around other Tor users around the world, thereby pseudo-anonymizing you when you access the dark web.
Is It Illegal To Use The Tor Browser?
When navigating the Dark Web, it is crucial to find legitimate websites toensure your safety and protectagainst scams and malicious activities. Engaging with illegal content not only puts you at risk of legal consequences but also supports criminal activities. By studying its past, we can better prepare for the future and develop effective strategies to navigate and secure this hidden part of the internet.
Some Linux distributions may also offer Tor Browser through their package repositories, but using the official download from the Tor Project website is generally recommended to ensure the latest version and integrity. For users running Windows, the installation process involves navigating to the official download page and selecting the download link for Windows, which will typically download an executable (.exe) file. Each relay in this circuit decrypts only one layer of encryption, obscuring the origin and destination of the traffic from any single point of observation. This encrypted data is then randomly bounced through a series of relays, operated by volunteers across the globe.
Interacting With Online Communities
Remember, navigating hidden services on the Dark Web requires a high level of caution and awareness. Illegal content refers to any material that violates local, national, or international laws, such as child pornography, drug trafficking, or hacking tools. When navigating the Dark Web, it is important to be aware of the presence of illegal content and take appropriate measures to avoid engaging with it. The Tor browser is a crucial tool for accessing the Dark Web securely and anonymously. A VPN, or Virtual Private Network, creates a secure and encrypted connection between your device and the internet. Understanding the history of the Dark Web provides valuable insights into its origins, development, and the challenges it poses for cybersecurity professionals.

Facebook’s dark web version allows users to access the site where it is banned or restricted. It does not share IP addresses or web search history to protect your privacy. It aims to advance research on terminal illnesses like cancer with access to unbiased scientific publications. Since Hidden Wiki maintains all kinds of websites, ensure you don’t open something you don’t want to see. It will offer you an additional layer of encryption to access the deep parts of the internet.
Tor Browser’s Levels Of Security
Launched in 2011, it is known to be one of the first online platforms of the dark web. Clario Anti Spy’s Data breach monitor scans for known breaches across the dark web and alerts you if your email is compromised. Our cookie files never contain personal data.
Enable Strong Security Settings

Don’t open attachments from untrusted sources, as they are a common vector for spreading malware. Confirm local circumstances before accessing the web via Tor. Hence, it’s advisable not to download files via Tor, especially from unknown sources. The last node (exit node), through which Tor routes your traffic, is delicate. Sometimes, you can access a website but won’t be able to login on your Tor browser. Tor is slower than standard browsers because it routes your traffic through multiple servers.
However, the most secure way to use Tor is via .onion sites, which are built exclusively for the Tor network. However, some websites consider Tor traffic suspicious and make users jump through several hoops, including CAPTCHAs. You will be connected to the Tor network, and then you can open onion websites and obfuscate your network activity. However, no matter how much you try to stick to legal websites, you can still land on illegal or highly disturbing content. The majority of users (over 90% as per our research) only need a Tor Browser for accessing .onion links; they don’t need to know about other methods.
Best Practices For Accessing The Dark Web
It is merely the content that is in a secure format, where the user must log in with a password or other credentials. It has the public websites, social media, news sites, and everything you engage with daily. For better safety and security, stick to only the verified .onion addresses or the addresses you trust. NordVPN is our #1 recommendation for dark web browsing because of its security, privacy, and performance. It’s just what you must do before accessing the Tor network. Think of the dark web as a hidden, members-only club for the internet.
Not all dark web services are genuine, and many scam “.onion” sites offer downloads infected with backdoors and Trojan horses. Some websites monitor and analyze the dark web for threat intelligence. There are reports of illegal services on the dark web, ranging from paid assassinations to the trafficking of sex and weapons.
Understanding The Risks: Why You Need This Guide
This prevents anyone—including your ISP—from knowing that you’re using the Tor network. Using a VPN alongside Tor adds an extra layer of security by hiding your IP address from Tor entry nodes and encrypting your traffic. Additionally, many Internet Service Providers (ISPs) flag Tor usage as suspicious and may block access to the network altogether.
It’s not as fast as NordVPN or Proton VPN, but for free access, it was smoother than expected — especially compared to some “free forever” VPNs that are borderline unusable. We got consistent performance on European and US free servers, and Tor connections stayed stable even when flipping between sites. It’s lightweight, privacy-focused, and gives you more flexibility than most other free options, without sacrificing speed or leaking your data. If you want a free VPN that’s low-key but still packs serious stealth, Hide.me is one of the best free VPNs we tested to access the dark web safely.
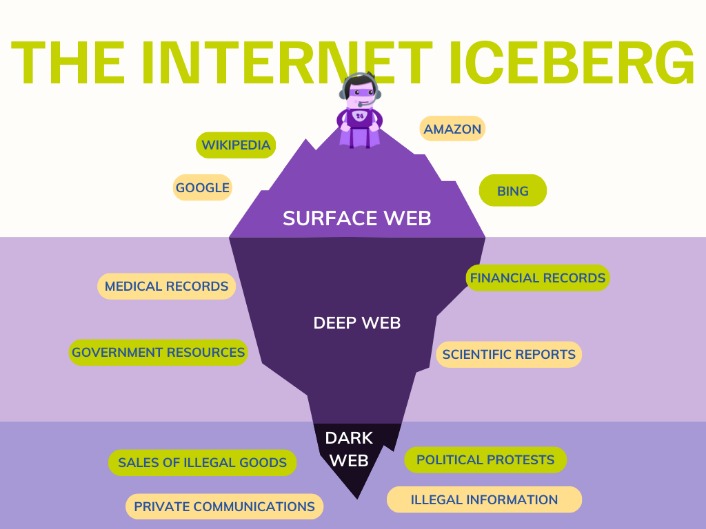
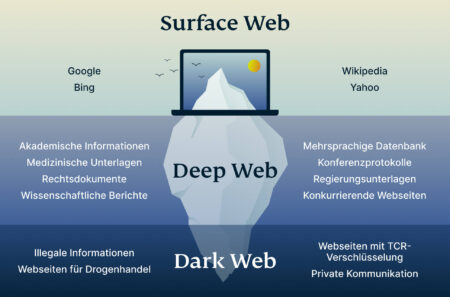
The dark web refers to sites that are not indexed and only accessible via specialized web browsers. This is how users can travel through enough tangential pathways and end up on a piracy site, a politically radical forum, or viewing disturbingly violent content. Everything from blog posts in-review and pending web page redesigns, to the pages you access when you bank online, are part of the deep web. On the larger deep web, its “hidden” content is generally cleaner and safer.
DefCon, ProPublica, the CIA, various libraries, and open-source software providers also feature in this area of the internet. To access a dark web resource, you will need to know its web address to the letter. It will normally take a while to connect because Tor — unlike other browsers — will route your traffic through different nodes. The Tor network is operated by thousands of volunteers worldwide who maintain the proxy servers that protect your identity.

This guide explains the secure and legal ways to explore the dark web, including what software to use, how to stay anonymous, and what precautions to take. Learning how to access the dark web safely is about using the right methods, protecting your privacy, and avoiding common risks. Learn how to access the dark web safely and legally with this step-by-step guide. I possess a keen interest in exploring and understanding the intricacies of malware, Advanced Persistent Threats (APTs), and various cybersecurity challenges. And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics. Don`t use your debit or credit card, stay away from dubious groups, and have fun while you’re at it.

In an age of rising cyber threats and data privacy concerns, knowing how to set up a VPN isn’t jus… Have you ever opened a laptop or connected a new monitor and wondered why everything looks blurry, o… Yes, via apps like Tor Browser for Android or Onion Browser for iOS, but desktops offer more security. A VPN combined with Tor provides better anonymity. Tor Browser masks your IP address and routes traffic through multiple servers.