We’ll also shed light on some of the legal uses of the dark web and show you how to access it securely in a detailed step-by-step guide. For over 40 years, PCMag has been a trusted authority on technology, delivering independent, labs-based reviews of the latest products and services. With expert analysis and practical solutions across consumer electronics, software, security, and more, PCMag helps consumers make informed buying decisions and get the most from their tech.
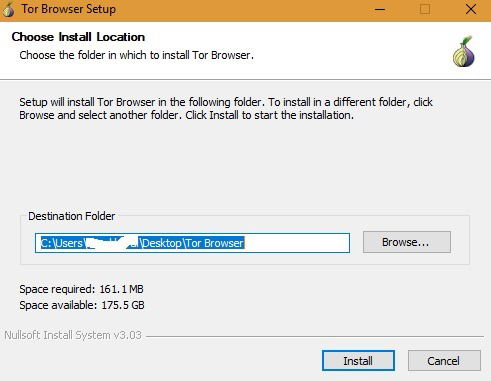
To enable it, check the Always connect automatically button on the homepage. For a limited time, new users who purchase any plan can claim 25% off their first order. The user will have the discount automatically applied after they click on it and check out. Please check your local laws to ensure your use of VPN complies with statutory requirements. Once the file is downloaded, run it to launch the installer and follow the prompt until the Tor browser is installed. Upon selecting the button for your operating system, you will be prompted to download the installer, which you should save to a folder.
This service is a good source of statistics if you have a school project requiring research on Tor and the dark web. However, note that the site only uses non-sensitive and public data for the metrics. The Tor Metrics is a good place to get more information about the Tor project. It collects data from the public Tor network and archives historical data of the Tor ecosystem.
How To Sell Counter-Strike 2 Skins Instantly? A Comprehensive Guide
The browser routes your traffic through a global network of volunteer-run servers (sometimes called nodes), encrypting your data and masking your IP address multiple times. Designed to be hidden from conventional search engines like Google or Bing, the dark web is a portion of the internet. Access to “.onion” domains and anonymous surfing made possible by specialised software like the Tor Browser allows entry only.
Our mission is to simplify navigation in the complex and evolving world of the darknet. Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more. Choosing the right tools isn’t just about convenience—it’s a crucial step toward ensuring your personal safety, digital privacy, and anonymity. In this guide, we’ll explore the best browsers and essential tools available in 2025, empowering you to access the dark web responsibly, securely, and with confidence.
Purchases through links on our pages may yield affiliate revenue for us. We review and list tools and products without bias, regardless of potential commissions. The internet is huge—even in its shadows—it is possible to wander legally there. Research of the dark web is legal as long as national or international laws are not broken.
Use Encrypted Communication Apps

Dark web domains tend to be inconsistent — new ones pop up and others disappear, which makes sense if they offer questionable or illegal goods and services. Tor Browser is available in multiple languages in a single multi-locale download, which can be changed using the menu in General settings. Yes, but only from the sites you connect to — instead of your IP address, they will only see the IP address of a Tor server. That said, using the Tor browser is not 100% safe, as the Tor network has a few security issues.
Myth 4: The Dark Web Is Inherently Dangerous To Visit
This includes evidence of any websites you visit, files you open, passwords you use, and even any other devices or networks you connect to. Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. Users who wish to gain access to such information are protected by the same anonymity the publishers of the content enjoy. Well-known news websites, such as ProPublica, have launched deep websites.
Step 7: Use Additional Security Tools
Instead of being targeted by sophisticated opponents, Tor and other darknets protect users from widespread surveillance. Tails isn’t just a browser—it’s an entire operating system designed specifically for anonymity. What’s most interesting is that you don’t need to install anything. You simply boot it from a USB stick, and that’s it—you can use it on almost any computer without leaving a trace.
Such data includes medical records, financial information, research papers, private forums and networks, and other content. Among the many benefits of using a VPN vs a proxy or Tor is that it provides full encryption for all the data you send and receive online. So not only is your web activity hidden, but you can mask your IP address by connecting via a wide range of global VPN server locations. Tails is a privacy-focused live operating system that you can boot from a USB stick. It is designed to be used without leaving a trace on your computer. It forces all internet connections to go through the Tor network.
How To Install Tor
This blog offers a complete guide on how to access the Dark Web using the Tor Browser, along with step-by-step instructions, security tips, legal warnings, and real-world examples. Tor was developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag. Tor was designed to protect American intelligence communications online. Tor Browser has since become a popular tool of journalists, activists, and others that may be subject to being monitored online. This is why I strongly advise anyone visiting the dark web to exercise the greatest of caution during their dark online travels.
What Is The Dark Web And How Do You Access It?
- We review and list tools and products without bias, regardless of potential commissions.
- This service is a good source of statistics if you have a school project requiring research on Tor and the dark web.
- When using a VPN for the dark web, your ISP will not be able to see that you are connected to a Tor node, only an encrypted tunnel to a VPN server.
- Merely downloading, installing and using the Tor Browser is not illegal.
- Damir has been mentioned in Mashable, Wired, Cointelegraph, The New Yorker, Inside.com, Entrepreneur, BeInCrypto, and other publications.
This is where an Onion website, like the Tor browser, comes in handy. It is the dark web’s version of Wikipedia with a massive links directory. You will find all the necessary .onion links to access any content or service on the dark web.
The software side of Tor Browser is certified to be safe by the Tor Project, trusted for its strong commitment to online anonymity and privacy. It develops open-source software that encrypts and routes internet traffic through a global volunteer network to protect users against surveillance and censorship. Any standard or “clearweb” sites will be just as safe with Tor as they are with other browsers, if not more so. Norton 360 Deluxe provides a comprehensive suite of protection that can help block malware and dangerous links in real time, and even detect scams using cutting-edge AI detection.
Is There A Tor Browser For Android?
Many reputable websites and news outlets like ProPublica and SecureDrop often share official domain addresses of onion sites on their pages. Some users also share links on encrypted apps like Telegram or Keybase that you can check. RiseUp is a top dark web website that offers secure email services and a chat option. It was created in 1999 as a secure communication platform for people and groups working on liberatory social change.

It is estimated that a substantial percentage of all hidden services are scams, further highlighting the need for extreme caution when navigating this environment. Therefore, users must approach all onion links with a high degree of skepticism and take measures to verify their authenticity whenever possible. The dark internet is designed to provide anonymity by keeping communication private through encryption and routing online content through multiple web servers. While the dark web is often depicted as an anarchic forum for criminal activity, that’s not necessarily true. The darknet is simply an anonymous space on the web that can be abused or appreciated in turn. That may seem an extreme way to browse the web, but such protections are increasingly worth considering, says Sarah Jamie Lewis, executive director of the Open Privacy Research Society.
Legitimate organizations and companies also sometimes establish a presence on the dark web. Law enforcement agencies monitor the dark web for stolen data and criminal activity, while major media organizations track whistleblowing sites for news. If you’re researching how to access the deep web, you’ll definitely come across Tor.