Naval Research Laboratory to enable secure and anonymous communication. Tor is by far the most widely used dark web network and is the biggest network in terms of content and activities. You need a specialized browser like Tor to access its websites. On the other hand, the deep web is the hidden part of the Internet that contains private or restricted content that is not indexed by search engines. In contrast, the surface web includes public websites that are easily found using search engines.

You need special tools to access the dark web, and the Tor Browser is the safest and most popular one. Using the dark web comes with serious risks for users who don’t take proper precautions. Always conduct your own research or check with certified experts before investing, and be prepared for potential losses. The content produced on this website is for educational purposes only and does not constitute investment advice or recommendation. The internet is huge—even in its shadows—it is possible to wander legally there.
The US Supreme Court has indicated that even casual browsing could lead to legal consequences. Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny. Think of it as the internet’s wild card.
Malware And Viruses
We believe everyone should be able to explore the internet with privacy.We are the Tor Project, a 501(c)(3) US nonprofit.We advance human rights and defend your privacy online through free software and open networks. With Tor Browser, you are free to access sites your home network may have blocked. Although it requires more work, it provides tech-savvy users with a more familiar interface with better security for accessing Tor through a proxy. I2P’s most attractive angle is to access its own internal eepsites, which are its version of .onion sites. You are solely responsible for complying with your region’s laws that apply and for ensuring your anonymity and security online. Regardless of your browser, accessing the dark web carries inherent risks, including potential exposure to malicious software and illegal activities.
Never Download Files
You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe. It blocks trackers, prevents user fingerprinting, encrypts data, and reroutes your browsing so no one can see where in the world you are. Part of what makes the dark web the dark web is that you can’t access it through your normal web browser, nor can you look something up on it via a Google search. The dark web comes with its own set of tools and services, including web browsers and search engines (which I’ll get on to in a moment). The dark web, which is what I’m discussing here, is a small subset of the deep web, and refers to websites that are specifically trying to stay out of sight. PCMag.com is a leading authority on technology, delivering lab-based, independent reviews of the latest products and services.
These forums look similar to those found on the clear web, but the content discussed and shared by the anonymous chatters can evade censorship on public sites and surveillance. As I mentioned above, the dark web is a decentralized, non-indexed network of web pages, and the sites don’t use standard URLs. Deep web content includes academic research papers, court documents, or medical records.
Our Network
In some countries, however, Tor is either illegal or blocked by national authorities. Tor does not support UDP, so don’t try to torrent free software ISOs, as it won’t work. Unlike Tor’s entry and exit nodes, bridge IP addresses are not publicly listed, making it difficult for web services, or governments, to blacklist those IP addresses. If you live in a regime that blocks Tor or need to access a web service that blocks Tor, you can also configure Tor Browser to use bridges. These services look at your IP address and guesstimate your country and language, but when using Tor, you will often appear to be in a physical location halfway around the world.
The Tor Browser – What Is It?
A VPN sends your web traffic to a server, which transmits it to the internet. Tor is not the same as a VPN, though both tools provide encryption and reroute your web traffic to another network. Tor Browser both anonymizes and encrypts your location through onion routing, better protecting your data when you get on the dark web. A proxy server acts as an intermediary between you and host services, while Tor is an encrypted network of decentralized servers. Your web traffic goes through thousands of layers of decryption when connecting to the internet via Tor Browser. Then get Avast Secure Browser for clean, fast, and easy private browsing.
How To Get On The Dark Web Using Tor Browser
IOS is the only exception, leaving iPhone and iPad users without the option to go to this part of the internet. In short, it’s ideal for torrenting, streaming, and gaming. While you can visit the obscure part of the internet without a VPN, it’s better to go with one. What about websites that restrict Tor connections? The downside is that some websites block Tor connections by detecting its exit node. This means you can go on the darknet privately while downloading torrents on the side.
- Your download and upload speeds may be slower, but that is the tradeoff for secure Internet browsing.
- The major issue with these websites is that a whopping 50 percent are fake, and there’s no way of telling for sure if they’ll deliver or not.
- We believe everyone should be able to explore the internet with privacy.We are the Tor Project, a 501(c)(3) US nonprofit.We advance human rights and defend your privacy online through free software and open networks.
- So, it’s worth using Firefox if you’re up for the tweaks needed.
- Powerful antivirus software with advanced Dark Web Monitoring Features like Norton 360 Deluxe can help keep your internet browsing private and secure.
How To Browse The Dark Web Legally & Safely?
In short, Brave is the perfect middle ground—fast, private, and easy to use without sacrificing convenience. That alone improves the browsing experience significantly. While it still occasionally connects to Mozilla to protect against malicious extensions, it doesn’t track you or collect your data. But if your goal is to build a secure and fortified environment for exploring the deep web, Subgraph is a serious and powerful option worth considering. It hasn’t received many updates lately, which may raise concerns for some users.
How To Access The Dark Web Using The Tor Browser?
If you must use one, ensure it’s a VPN with a strict, independently audited no-logs policy. A VPN app opens another potential vulnerability, as it can log the sites you visit via Tor. A common inquiry from Tor users is if they should use a VPN to add an extra layer of protection.

- The dark web comes with its own set of tools and services, including web browsers and search engines (which I’ll get on to in a moment).
- The web uses onion routing, which caches your data through multiple layers of encryption over multiple networks.
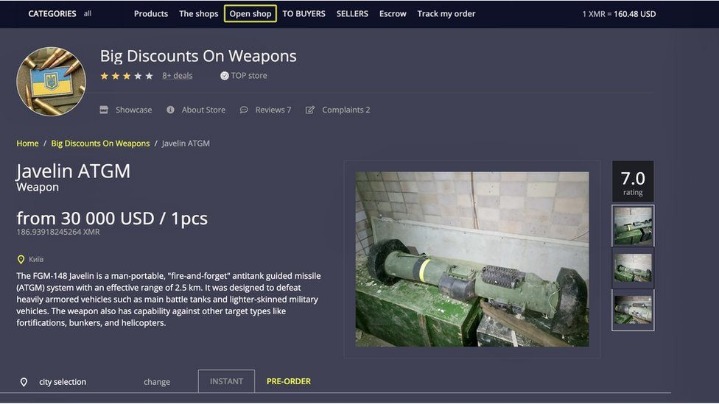
- The inherent anonymity of the place attracts scammers and thieves, but what do you expect when buying guns or drugs is your objective?
- While Tor Browser enhancing your anonymity online, it does not protect users from all dangers of the web.
- Another private cryptocurrency you’ll find being used is Monero, which prides itself on being untraceable.
I tend to read app privacy policies to see what kind of data companies collect, and as a result of those findings, I don’t use many mobile apps. I like testing new software for work, but I’m less “plugged in” to the internet than I used to be. For example, Briar is an extremely private chat app designed to help journalists communicate anonymously with sources.
Because of this reason, it is quite easy to encounter fraudulent or malicious websites and you need to take a cautious approach to manually avoid them. By traditional websites, we mean websites with domains like .com, .org, .gov, etc., and easy-to-remember names, like google.com. Dark Web also does not have traditional websites like you find on the Surface web.

Using a VPN in conjunction with the Tor Browser is an excellent way to keep your online travels secure and private. Then the Tor anonymity network relays further obfuscate your true location, as the browser relays your browser traffic through several relay locations. A VPN keeps all of your online activities – including your web browsing, online gaming, streaming, and file-sharing – undercover and safe from being tracked or recorded. The Tor Browser prevents your ISP from seeing what websites you’re visiting, but it does not prevent the ISP from seeing that you’re using Tor. If you need to protect or enhance your streaming, gaming, or torrenting activities, a Virtual Private Network (VPN) is a much better option as a secure connection to the net. Because of the relaying of data through the onion nodes, and the encrypting and decrypting taking place at each node, your internet connection will slow considerably.
Similarly, people in countries with strict internet access and usage regulations must use Tor clients or virtual private networks (VPNs) to access some public websites. It includes websites, databases, and other online resources indexed by search engines and is easily discoverable by users. The Hidden Wiki is a huge directory that provides links to Onion websites with various services, secure email, secure social networks and more. Once Tor Browser is successfully connected to the Tor network, users can begin to explore what are known as onion services, often referred to as websites on the dark web.